Introducing xpidump
Clermont-Fd Area, FranceI wrote xpidump to give a human-readable summary of some information about a Firefox add-on. It is designed to answer these two questions: is the add-on likely1 signed? And if so, how?
This tool takes an XPI file as input. XPI files are Firefox add-ons packaged
as ZIP archives with the .xpi file extension. xpidump currently extracts
information from up to 4 files in an XPI (depending on what is available in the
archive):
manifest.json: this JSON file defines the add-on. It is required in any add-on (packaged or not, signed or not).META-INF/mozilla.rsa: this binary file is a PKCS#7 signature. Any signed add-on should have this file (in addition toMETA-INF/mozilla.sfandMETA-INF/manifest.mfbut xpidump doesn’t read them).META-INF/cose.sig: this binary file is a COSE signature2. It might not be present when the add-on isn’t signed or relatively old3. There should also be aMETA-INF/cose.manifestfile when this file exists.mozilla-recommendation.json: this JSON file is generated by Mozilla’s signing service Autograph when an add-on is signed with recommendation states. This is how Firefox knows that an add-on is recommended for instance. It might or might not be present.
xpidump is both a command-line tool and a web app since the latter is usually more convenient (no need to install anything). It’s written in Rust, and compiled to WebAssembly for the web app. You can try it at: williamdurand.fr/xpidump/.
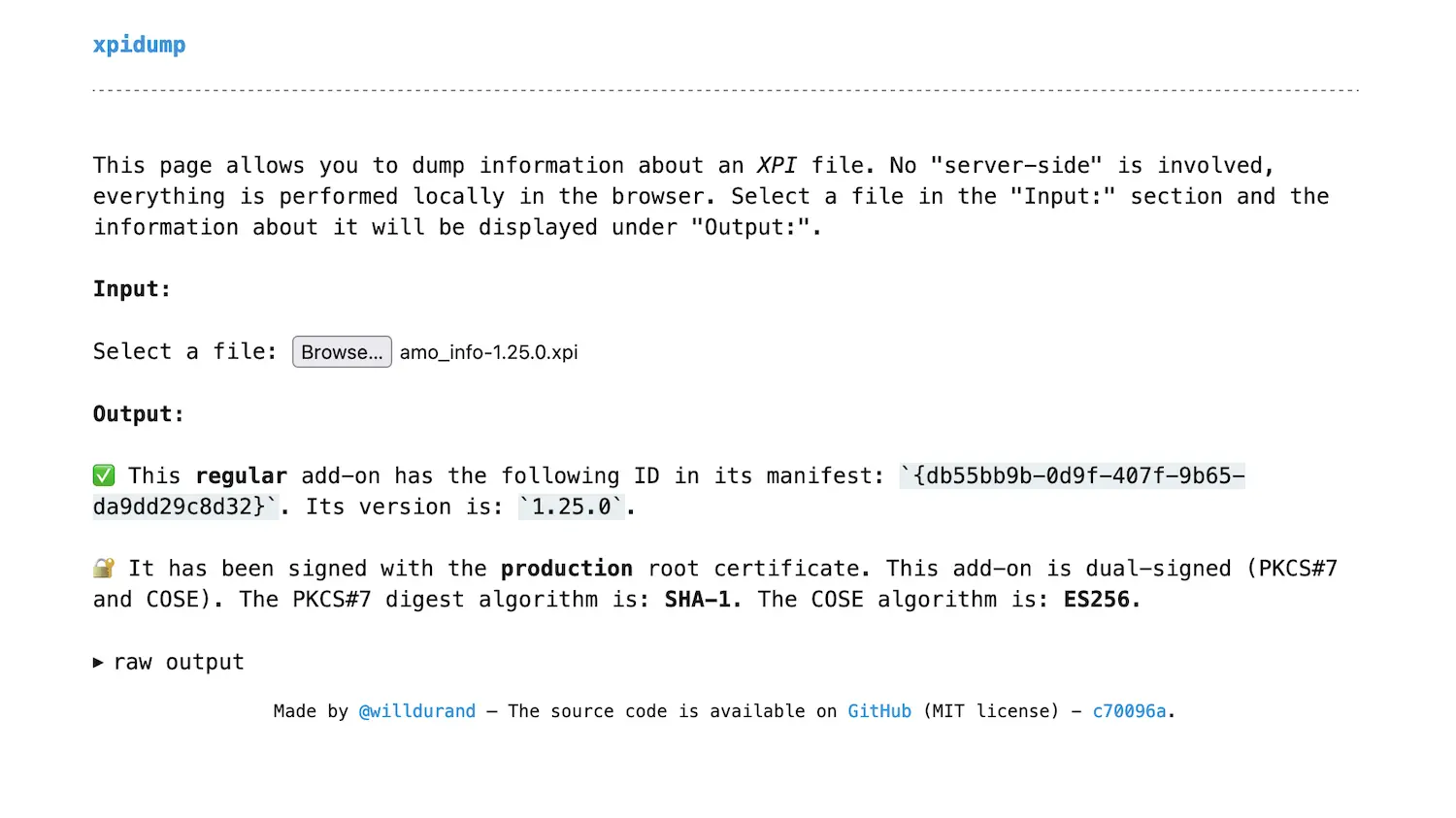 xpidump is available in the browser thanks to WebAssembly!
xpidump is available in the browser thanks to WebAssembly!
The code is published on GitHub under the MIT license, see: willdurand/xpidump. I don’t have any more plans for this weekend-ish project, it’s doing what I wanted it to be doing… Let me know if you have ideas, though.
One more thing while we’re here… If you want a tool to read the entire content of any XPI file and get tons of information, you want to use CRX Viewer created by my brilliant colleague Rob!
-
This tool doesn’t verify the signature, so it cannot guarantee that the add-on is correctly signed. ↩
-
Well, a COSE sign message with a signature and serialized with CBOR, though we should probably refer to the protocol as COSEish because of this issue. ↩
-
Mozilla started to dual-sign add-ons in 2019. ↩
ℹ️ Feel free to fork and edit this post if you find a typo, thank you so much! This post is licensed under the Creative Commons Attribution-ShareAlike 4.0 International (CC BY-SA 4.0) license.
Comments
You can interact on Mastodon or send me an email if you prefer.